The days of a security guard at the front desk and a few cameras in the parking lot are long gone. Today's Chief Security Officers are managing complex ecosystems that span physical safety, digital infrastructure, emergency response, and business continuity often across multiple locations and venue types.
In short, corporate security is the practice of protecting a company’s personnel, physical and intellectual property and information systems from both internal and external threats.
Whether you're protecting a sprawling retail portfolio, a hospital system, a corporate campus, or a major stadium, the fundamentals remain the same: you need to keep people safe, protect assets, and respond effectively to incidents in a way that doesn’t prevent visitors from enjoying their experience.
And protecting your venue, its assets and its visitors has never been more important. The 2025 World Security Report found that:
And in total, the companies surveyed lost close to $1 trillion in revenue due to physical security incidents.
This guide breaks down what modern corporate security looks like, the unique challenges different venues face, and the technology and strategies Chief Security Officers are using to stay ahead of threats while maintaining operational efficiency.
Interested in seeing how Mappedin can transform your venue's private security, streamline operations and drive better visitor experiences? Book a personalized demo. →
What modern corporate security looks like today
Corporate security has evolved into a multi-layered discipline that goes beyond traditional physical protection.
Modern Chief Security Officers oversee integrated operations that include access control, surveillance, emergency response, threat assessment, compliance management, and increasingly, coordination with IT teams on cyber-physical security threats.
Because threat types have expanded, so has the role of the CSO. Active shooter scenarios, medical emergencies, natural disasters, cyber attacks that affect physical systems, workplace violence, and even reputational risks all fall under the security umbrella now. And while security teams uphold a duty of care, the venue needs to maintain a positive, stress-free experience for employees, visitors and customers at the same time.
Download the State of Venue Experience →
The expanded role of the Chief Security Officer
Today's Chief Security Officers manage four core areas:
Physical safety operations
This is the foundation: access control, surveillance, patrol operations, and emergency response.
But it's no longer just about having security personnel at entry points. Modern physical safety integrates with building management systems, uses AI-powered analytics to identify potential threats, and coordinates across multiple locations in real-time.
Risk management and compliance
Chief Security Officers are responsible for identifying vulnerabilities, conducting threat assessments, and ensuring compliance with industry regulations. In healthcare, that means HIPAA considerations. In retail, it's loss prevention coordination. In corporate offices, it's protecting executive travel and sensitive information.
Incident response and business continuity
When something goes wrong—and something will go wrong—the CSO needs systems in place to respond quickly, coordinate across teams, document everything for compliance, and learn from each incident to prevent future occurrences.
Stakeholder communication
Chief Security Officers increasingly serve as the bridge between security operations and executive leadership. That means demonstrating ROI, explaining security investments, and sometimes making the case for why visible security measures are necessary even when they create friction
Corporate security vs. facility management
There's often confusion about where security responsibilities end and facility management begins. The reality is that modern security operations overlap significantly with facilities, IT, and operations teams.
Facility managers handle building systems, maintenance, and space planning. Security teams rely on those same building systems; access control is tied to door hardware, surveillance systems need network infrastructure, emergency communication platforms integrate with building PA systems.
The most effective corporate security programs treat this overlap as an opportunity for collaboration. Chief Security Officers who work closely with facility managers can implement security measures that feel seamless rather than bolted on.
When you're redesigning a lobby or adding a new building to your campus, involving security early means you can design safety into the space rather than retrofitting it later.
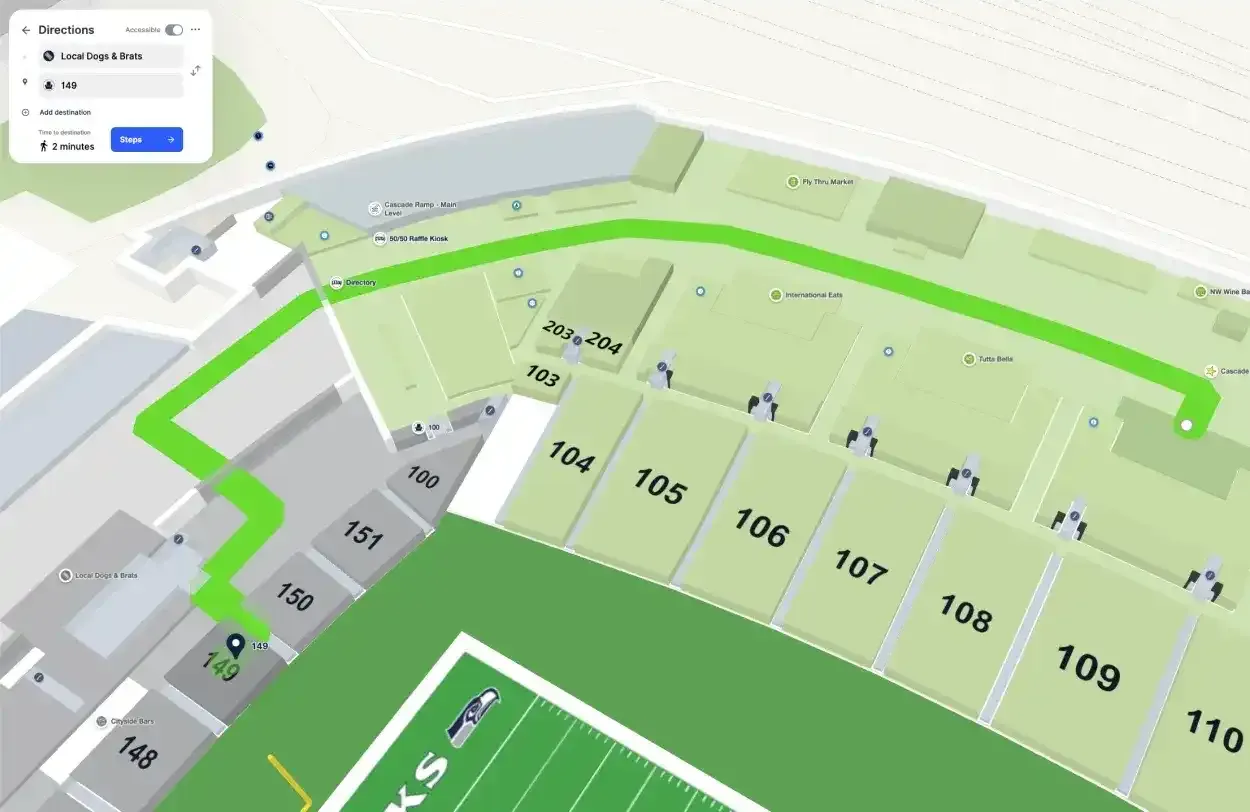
Corporate security challenges by venue type
Not all venues face the same security challenges. For example, a hospital's security concerns look nothing like a shopping mall's, and what works for a corporate office campus won't translate to a massive sports venue.
Understanding these differences helps Chief Security Officers tailor their approach.
Mall security and retail portfolios
Shopping malls present unique security challenges because they're open-access environments designed to welcome as many people as possible. Malls and large retail venues have a duty of care to protect tenants, shoppers, and assets.
The biggest challenge in mall security is coordination.
CSOs are managing security across dozens of independent retailers, each with their own loss prevention teams and priorities. Effective mall security requires centralized incident management that gives individual tenants visibility into security events while maintaining operational control at the portfolio level.
Parking structures are another major vulnerability. They're often poorly lit, isolated from the main shopping areas, and difficult to monitor effectively. Modern mall security operations use a combination of increased lighting, strategically placed cameras with analytics capabilities, and mobile patrol patterns that eliminate predictability.
Hospital security
Hospital security operates at the intersection of safety and care, which creates complications that don't exist in other environments. Security personnel need to be trained in de-escalation techniques because they're often dealing with people in crisis.
The emergency department is ground zero for hospital security challenges. It's a 24/7 operation that sees everything from minor injuries to violent trauma cases, and tensions run high. Effective hospital security in the ED means having personnel who understand that a combative patient might be experiencing a medical crisis, not just being difficult.
Restricted areas add another layer of complexity. Each area has different requirements, and security teams need to enforce those requirements without creating an institutional feel that undermines the healing environment.
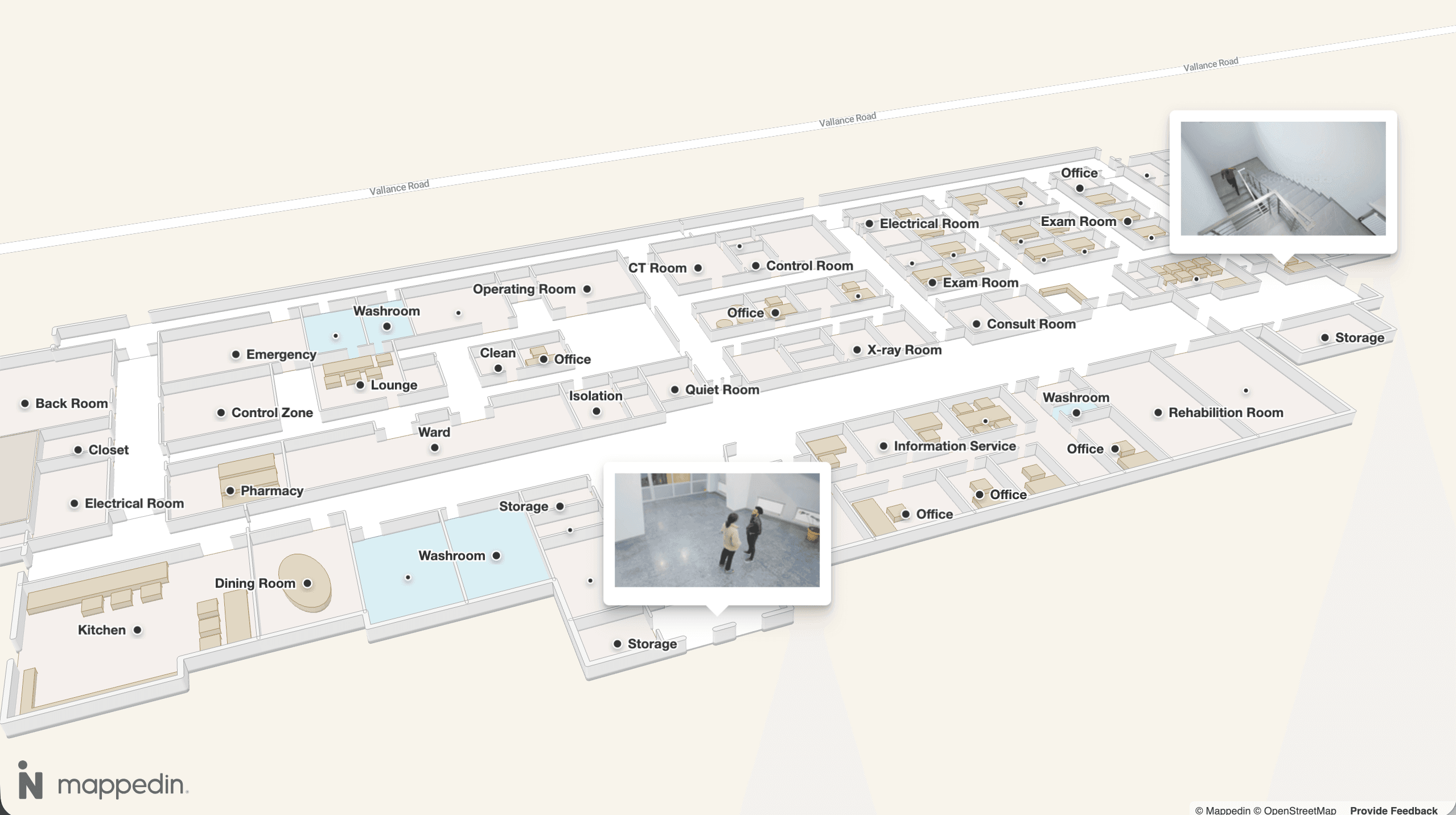
Office security for corporate workspaces
Corporate office security has been completely reshaped by hybrid work. The traditional model – employees badge in every morning, visitors sign in at the front desk, everyone leaves by 6 PM – no longer matches how people work.
Access control in hybrid environments means dealing with employees who might come to the office twice a week or twice a month, contractors who need temporary access, visitors who need to be tracked but not treated like security threats, and executives who expect frictionless entry even with enhanced security measures.
The challenge multiplies across multiple buildings. A corporate campus with 10 buildings might have 50+ entry points, each requiring monitoring, access control hardware, and coordination with the central security operations center.
Chief Security Officers need to decide which entrances stay open during business hours, which require badge access 24/7, and how to handle after-hours access for cleaning crews and maintenance.
Visitor management has also become particularly complex in corporate office environments. Companies expect to know who's in the building at all times for emergency response, data analytics and security purposes.
Stadium security
Stadium security has unique needs than other types of large venues. When you're responsible for 70,000 people entering a venue over a 120-minute window, your security approach needs to prioritize throughput without compromising safety.
Entry screening
Bag checks and metal detectors slow things down, but they're necessary. The key is having enough screening lanes, training staff to move people through quickly, and using clear signage so guests know what to expect before they reach the checkpoint.
Crowd management
Security personnel need to identify potential problems like overcrowding in concourses, altercations between fans, and medical emergencies and respond without creating panic or disrupting the event for thousands of other guests.
Law enforcement coordination
Most venues work closely with local police for major events, but the division of responsibilities needs to be clear. Stadium security typically handles inside the venue, while police manage perimeter security, traffic control, and any incidents that rise to the level of criminal activity.
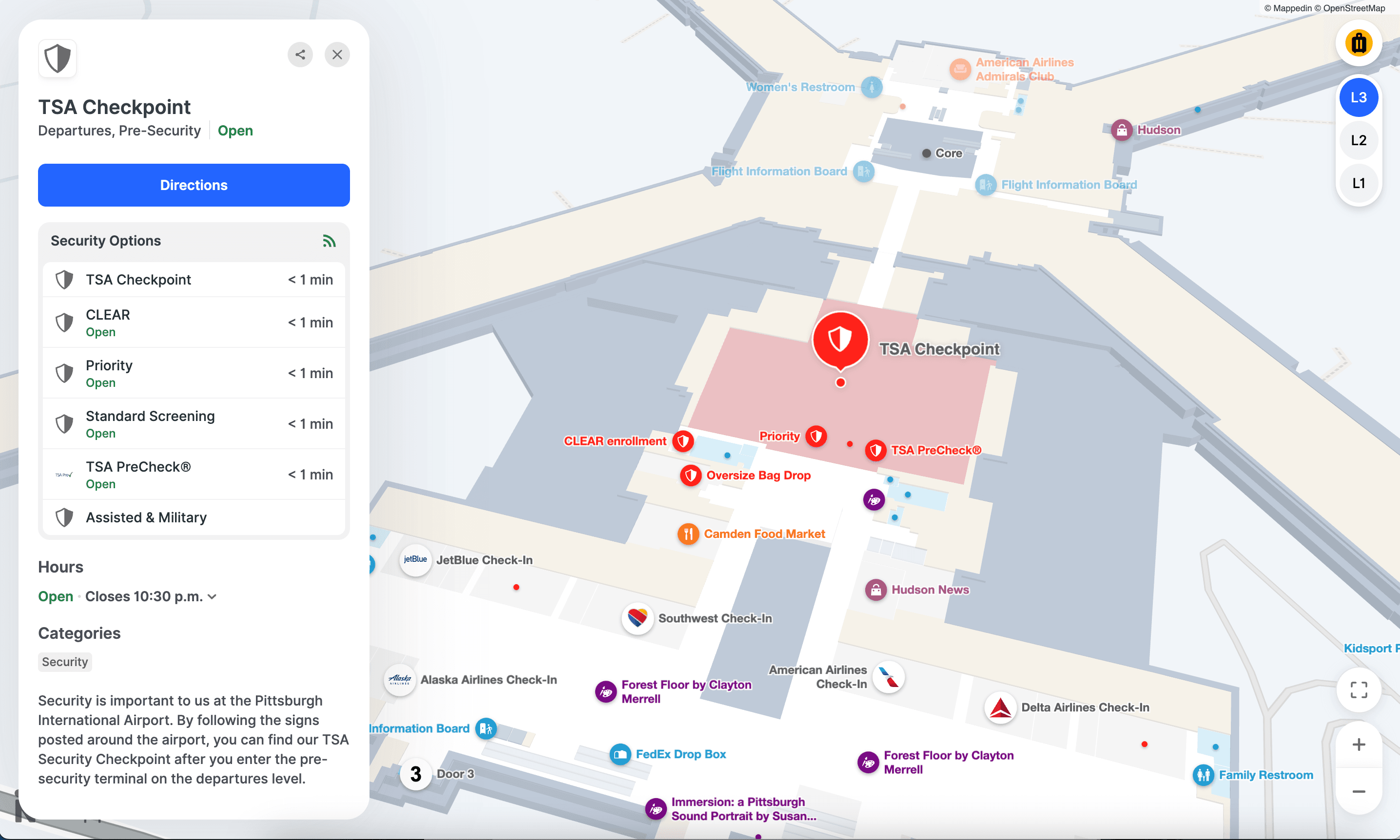
Airport and corporate aviation security
Airport security is multilayered by design—and necessity. While TSA handles passenger screening at commercial terminals, airports and airlines are still responsible for securing the facility, managing access to restricted areas, and coordinating with federal partners.
Corporate aviation security—private terminals and FBOs (fixed-base operators)—operates under different rules but with equally high stakes.
These facilities serve executives, high-net-worth individuals, and sometimes government officials. Security needs to be tight enough to protect high-value targets without creating the kind of screening bottlenecks that defeat the purpose of private aviation.
Landside security is just as essential. The areas outside of TSA checkpoints (ticketing, baggage claim, ground transportation) are accessible to anyone and have been targets in multiple international incidents. Modern airport security extends far beyond the checkpoint.
Building an effective corporate security program
When thinking through a corporate security strategy, Chief Security Officers don’t often have the luxury of a blank slate or endless time. CSOs are typically trying to make an existing operation better through tighter security, faster response times, lower costs, better employee experience.
Here's how to approach it systematically.
Risk assessment and planning
- Understand the scope of what you're protecting. This sounds obvious, but many security programs are built on assumptions that were never validated.
- Walk every location. Not a quick tour with the facility manager—actually walk it the way an attacker would. Where are the blind spots? Which doors are supposed to be secure but get propped open for convenience? Which areas see the most foot traffic and therefore the most opportunity for incidents?
- Talk to the people who work there. Security guards see things that never make it into incident reports. Front desk staff know which visitors make them uncomfortable. Maintenance crews know which areas are isolated and poorly lit. These conversations reveal vulnerabilities that don't show up on floor plans.
- Prioritize risks based on likelihood and impact. Every venue has dozens of potential security concerns. You can't address them all at once, so focus on the ones that are most likely to occur or would cause the most damage if they did:
- An active shooter scenario is low probability but catastrophic impact.
- Workplace disputes that escalate are higher probability and moderate impact.
- Theft and vandalism are high probability and low impact.
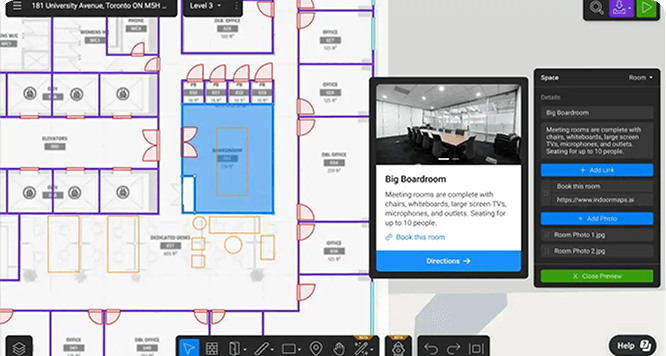
Corporate security technology essentials
Technology doesn't replace good security practices, but it dramatically scales what a security team can do. The key is choosing tools that integrate with each other and match how your team works.
Access control systems determine who can enter which areas and when. Modern systems usually include mobile credentials, biometric authentication for high-security areas, and integration with HR systems so that access automatically updates when employees change roles or leave the company.
Video surveillance today often includes technology that can detect unusual behavior, identify overcrowding, flag vehicles in restricted areas, and alert security teams to potential problems before they escalate. The key is using these tools to augment human judgment rather than replace it.
Emergency communication platforms let you reach employees, visitors, and security teams instantly during a crisis. This might mean sending a mass notification about a weather emergency, alerting employees to shelter in place during an active threat, or coordinating with security teams across multiple buildings during an incident.
Security incident management software ties everything together. When something happens, you need a way to log it, coordinate the response, track what actions were taken, and analyze the outcome. Modern incident management platforms integrate with access control and surveillance systems, shows the location of security teams in the field, and generate real-time analytics reports for compliance and executive review.
Evaluating security software
CSOs should focus on these critical capabilities when evaluating corporate security software.
- Mobile-first design: Your security teams are in the field, not sitting at desks. The software needs to work seamlessly on phones and tablets, with offline capability for areas with poor connectivity.
- Integration flexibility: The system should connect with your existing access control, surveillance, and building management systems. Proprietary platforms that don't integrate well with existing systems create information silos.
- Customizable workflows: Every venue is different. You need software that adapts to how your team works, not software that forces you to change your processes to match what the vendor thinks security should look like.
- Reporting and analytics: The system should make it easy to generate reports on incident frequency, response times, resolution rates, and other KPIs that demonstrate security program effectiveness.
Team building and training
Security teams are only as effective as their training and leadership. Follow these three pillars to security team training.
- De-escalation training should be mandatory. Most security incidents require someone who can read a situation, communicate clearly, and calm things down before they escalate. This is especially important in environments like hospitals and schools where security teams interact with vulnerable populations.
- Technology training is increasingly important as security operations become more sophisticated. Officers need to know how to use incident management software, monitor surveillance systems, operate access control interfaces, and coordinate via mobile devices. This requires ongoing training, not just a one-time orientation.
- Third-party vendor management is a reality for most security operations. Whether you're using contract security officers, monitoring services, corporate security software, or specialized consultants, you need clear standards for performance, regular audits to ensure they're being met, and direct lines of communication so that contracted staff feel like part of the team rather than outsiders.
How to measure corporate security effectiveness
Chief Security Officers need to prove that security investments deliver value. That means tracking and reporting on metrics that matter to executive leadership.
6 key performance indicators for corporate security teams
1. Incident frequency trends show whether your security program is preventing problems or just responding to them.
Track incidents by type and location over time. If break-ins at one facility are increasing while decreasing at others, that tells you something about the effectiveness of security measures at that location.
2. Response times measure operational efficiency.
- How long does it take from when an alarm goes off to when a security officer arrives on scene?
- How long from when an incident is reported to when it's resolved?
Faster isn't always better as some incidents require more thorough investigation, but consistently slow response times indicate problems.
3. Resolution rates track what percentage of incidents are successfully resolved versus escalated or left unresolved.
This matters for both security effectiveness and employee confidence in your security program.
4. Training compliance ensures your team maintains the skills they need.
Track completion rates for mandatory training, certifications that need renewal, and ongoing education requirements.
5. Loss prevention metrics translate directly to ROI in retail environments.
For example, a goal may be to reduce shrinkage by 2% through better security protocols, translating into income.
6. Insurance premium reductions are another tangible benefit.
Insurers offer lower premiums for facilities with strong security programs, comprehensive incident documentation, and demonstrated risk management practices.
What's next: The evolution of corporate security
The role of corporate security continues to expand beyond traditional security operations into broader risk management and strategic planning.
Physical-cyber security convergence is accelerating. When building management systems, access control, and surveillance cameras all run on IP networks, they become potential cyber attack vectors. Chief Security Officers increasingly work alongside CIOs to secure these systems against both physical and digital threats.
In parallel, AI-powered predictive analytics are moving security from reactive to proactive. Instead of responding after incidents occur, modern security operations use data from access control systems, surveillance cameras, and incident reports to identify patterns that suggest elevated risk and take preventive action.
The most effective Chief Security Officers position themselves as business enablers, not obstacle creators. Security measures should facilitate business operations while managing risk, not prevent things from happening. That requires understanding the business deeply enough to know which security measures will be accepted and which will be circumvented, then designing systems that people will actually use.
Interested in seeing how Mappedin can transform your venue's private security, streamline operations and drive better visitor experiences? Book a personalized demo. →
Share
